The process of making copies of files which can be used to restore the original copy in the event of data loss is called file
(i) The home network of a family has internet access. A server configured to control user access to the network.
State two problems that will likely happen if the children in the family have uncontrolled access to the internet
(ii) The home network of a family has internet access. A server configured to control user access to the network.
Suggest how the problems in 1(a)(i) can be prevented.
1(b) The home network of a family has internet access.
A server configured to control user access to the network.
Give one reason for the user control access
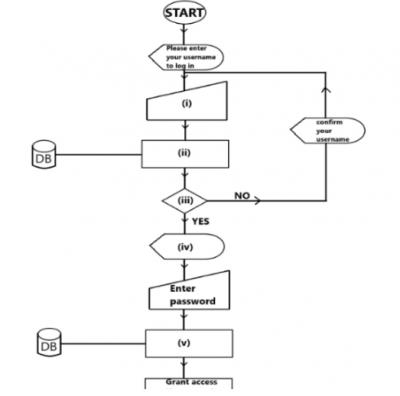
c(i) To have access to the network, each user logs in with a username and password. The flowchart in Figure 1 illustrates the authentication process required to log in. Use the information below to complete the flowchart by placing the letters A to E in the appropriate flowchart symbol numbered (i) to (v) :
A - "Please, enter password to log in"
B - Is the username found?
C - Search the username in the database.
D - Check the password.
E - Enter the username.
(i) ___________________________________________
c(ii) A - "Please, enter password to log in"
B - Is the username found?
C - Search the username in the database.
D - Check the password.
E - Enter the username.
(ii) ___________________________________________
c(iii) A - "Please, enter password to log in"
B - Is the username found?
C - Search the username in the database.
D - Check the password.
E - Enter the username.
(iii)___________________________________________
c(iv) A - "Please, enter password to log in"
B - Is the username found?
C - Search the username in the database.
D - Check the password.
E - Enter the username.
(iv) ___________________________________________
c(v) A - "Please, enter password to log in"
B - Is the username found?
C - Search the username in the database.
D - Check the password.
E - Enter the username.
(v) ___________________________________________
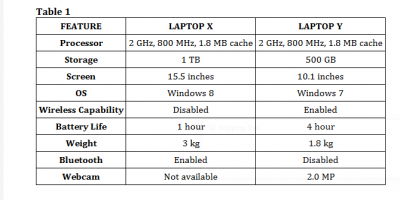
a - Table 1 shows the specification of two laptop computers. Use the table to answer questions 2(a) and 2c .
A journalist makes long trips by train as part of official assignments. The journalist also needs to make live communication with editors.
Which of the two laptop computers is more suitable for this journalist?
b - A journalist makes long trips by train as part of official assignments. The journalist also needs to make live communication with editors.
State three features of the chosen laptop in 2(a) that makes it better.
c - A journalist makes long trips by train as part of official assignments. The journalist also needs to make live communication with editors.
Give one reason for choosing each of the features stated in 2(b)
a - A principal asked the secretary to typeset a document containing some confidential information in Microsoft Word. The principal wants the document to be typed in such a way that when it is opened, the confidential information will be hidden from other users.
Highlight the steps the secretary would take to hide the confidential information in the document.
b - A principal asked the secretary to typeset a document containing some confidential information in Microsoft Word. The principal wants the document to be typed in such a way that when it is opened, the confidential information will be hidden from other users.
Outline the steps the principal would take to display the hidden text in 3(a) for viewing.